Sunday, December 24, 2006
VMware Workstation 6.0 BETA...
The VMware Workstation 6.0 beta has finally gone public, and looks to have some great new features. I'll be running it up in my Vista x64 build to shake out the bugs... looks like there are some great new features, although disappointly the VIX API isn't compatible with the VI3 SDK... it would've been great if the VIX API at least supported C# but from what I can see it's a C only affair, or scriptable (via what I don't know... I guess Perl and COM).
WSS 3, and Merry Xmas!
Funnily enough WSS 3 was already out when I last posted (gee, has it been that long!)... you can download it here. XNA Game Studio Express also went GA, which is pretty cool... I hope to find some time to mess with that.
In other news I've installed Vista (x64) courtesy of a new MSDN subscription, however after the initial build I must admit I still haven't used it much... there's just something I don't like about it, that I can't put my finger on. Maybe is was the wierdness around configuring networks, or just the general unfamiliarity with a lot of the new services... I dunno, they just seem superfluous. If it wasn't for C# and Half Life 2, I don't think I'd use Windows at all really... wonder how much Microsoft is paying Valve to stop them from releasing a Linux client / Linux version of Source ;-)
Anyways, have a merry xmas!
In other news I've installed Vista (x64) courtesy of a new MSDN subscription, however after the initial build I must admit I still haven't used it much... there's just something I don't like about it, that I can't put my finger on. Maybe is was the wierdness around configuring networks, or just the general unfamiliarity with a lot of the new services... I dunno, they just seem superfluous. If it wasn't for C# and Half Life 2, I don't think I'd use Windows at all really... wonder how much Microsoft is paying Valve to stop them from releasing a Linux client / Linux version of Source ;-)
Anyways, have a merry xmas!
Tuesday, November 28, 2006
VM security - new threats on the horizon...
Here's a VERY interesting read from the legendary Ed Skoudis and Tom Liston, about some recent observations in attack code. Basically, code is surfacing that detects whether the machine is 'real' or virtual. The authors offer an explanation to the effect of "attackers perceive that a lot of honeypots are running as VM's, therefore their code doesn't execute on VM's in an effort to avoid detection".
Of course, VMware marketing are already trying to put a "VM's are more secure than physical boxes" spin on it, but really they are doing themselves more harm than good... I can only assume they didn't see the last few slides that demonstrate the isolation of VM's is somewhat questionable (I'm sure you'll agree when you see them). VM isolation is something VMware has aggressively defended in the past... I remember a whitepaper they released not so long ago in response to someone who was questioning storage isolation. That person clearly had no idea how VMware actually works, unlike Liston & Skoudis.
Of course, VMware marketing are already trying to put a "VM's are more secure than physical boxes" spin on it, but really they are doing themselves more harm than good... I can only assume they didn't see the last few slides that demonstrate the isolation of VM's is somewhat questionable (I'm sure you'll agree when you see them). VM isolation is something VMware has aggressively defended in the past... I remember a whitepaper they released not so long ago in response to someone who was questioning storage isolation. That person clearly had no idea how VMware actually works, unlike Liston & Skoudis.
Microsoft Patterns & Practices Security How Tos...
Here's a bunch of very handy articles from the Patterns and Practices group at Microsoft... they will go a long way towards helping infrastructure engineers work with application developers to ensure secure application architecture and deployment.
I don't know how many arguments I've had with developers who had no idea about what they were actually proposing to deploy from an infrastructure security standpoint (much worse than the usual 'must run with admin' demands), I'll be sure to point them at this link when relevant in the future!
I don't know how many arguments I've had with developers who had no idea about what they were actually proposing to deploy from an infrastructure security standpoint (much worse than the usual 'must run with admin' demands), I'll be sure to point them at this link when relevant in the future!
Saturday, November 25, 2006
Let the gIntegration begin!
New Microsoft releases coming thick and fast...
The final WAIK has been released, get it here. I know a ton of people have been waiting for that... finally Windows PE 2.0 is available for the masses.
I'm still holding out for WSS 3.0 though. I was hoping they would have released it when Office 2007 was RTM'ed, but I guess we'll be waiting for the GA of 2003 SP2. Although from reports about the quality of the 2003 SP2 RC, I guess I could probably use whatever is in that!
I'm still holding out for WSS 3.0 though. I was hoping they would have released it when Office 2007 was RTM'ed, but I guess we'll be waiting for the GA of 2003 SP2. Although from reports about the quality of the 2003 SP2 RC, I guess I could probably use whatever is in that!
Thursday, November 16, 2006
Oh, and PowerShell 1.0 has finally made GA!
I was on the early beta's of PowerShell (I still hate the name, although the name 'Monad' did lend itself to an unfortunate gnu-ified name), and am stoked to see it finally hit 1.0. What's also awesome is to see Jeffrey Snover's enthusiasm seems have gone viral inside Microsoft... PowerShell is up in everything.
THe latest video on Channel9 shows PowerShell as applied to IIS7, as well as a few other cool cmdlets from powergadgets. That stuff is gold... great job with the architecture Jeffrey, making PowerShell so extensible via C# is the best thing to have happened to the shell, ever.
So go grab PowerShell now, and check out the video!
THe latest video on Channel9 shows PowerShell as applied to IIS7, as well as a few other cool cmdlets from powergadgets. That stuff is gold... great job with the architecture Jeffrey, making PowerShell so extensible via C# is the best thing to have happened to the shell, ever.
So go grab PowerShell now, and check out the video!
Smart move, Citrix....
I don't know if this move by Citrix is possibly in response to the upcoming Longhorn release, but it is certainly looooooooooooooong overdue. I've been wanting to install and mess around with PS4 for ages at home, now I finally can!
Perhaps they have finally realised that putting Enterprise software in the hands of enthusiasts pays off... those kinds of people are often the ones engineering / architecting solutions. If not for this developer license program, I would have thrown myself into Longhorn Terminal Services and had a fairly one sided view... now I'll be looking at it with a much more critical eye.
Perhaps they have finally realised that putting Enterprise software in the hands of enthusiasts pays off... those kinds of people are often the ones engineering / architecting solutions. If not for this developer license program, I would have thrown myself into Longhorn Terminal Services and had a fairly one sided view... now I'll be looking at it with a much more critical eye.
Thursday, November 09, 2006
VI3 Storage Performance...
An as yet unidentified company is planning to release some interesting data soon surrounding performance of the various datastore options in VI3... namely local SCSI, FC, iSCSI and NFS.
Without stealing too much of their thunder, apparently an NFS mounted VMFS volume is 4 times faster than an iSCSI one!!! I'll be interested to see the details when the data comes out... there are substantial performance differences in the few iSCSI implementations around, and various tweaks that can be made to improve performance.
Meanwhile, I'm configuring my Ubuntu iSCSI target with NFS as well, and plan to do some testing of my own... stay tuned!
Without stealing too much of their thunder, apparently an NFS mounted VMFS volume is 4 times faster than an iSCSI one!!! I'll be interested to see the details when the data comes out... there are substantial performance differences in the few iSCSI implementations around, and various tweaks that can be made to improve performance.
Meanwhile, I'm configuring my Ubuntu iSCSI target with NFS as well, and plan to do some testing of my own... stay tuned!
Tuesday, November 07, 2006
.NET 3.0 Released / Vista SDK Final Released!
Funnily enough, .NET 3.0 has gone GA and so has the Vista SDK!
.NET Framework 3.0
Vista SDK (scroll to the bottom and grab the DVD ISO)
w00t!
.NET Framework 3.0
Vista SDK (scroll to the bottom and grab the DVD ISO)
w00t!
Ubuntu the Enabler! Moss the Interrupter!
You have to go to Ginkaku-ji in Kyoto to get that second bit...
Anyway, I'm decidedly 'over' Linux as a desktop... I'll be running XP into the ground and wait for the next version of Windows, which will be out before XP support ends if Microsoft stick to their "no more 5 years between OSes" mantra. Besides, all the stuff that's interesting to me in Vista / Longhorn (ie .NET 3.0) will be available on XP anyway. I could care less about Aero, DX10 games won't be out for ages, and my shit is locked down so security isn't an issue.
But back to the topic of the post - Ubuntu the Enabler! I've been playing more and more with VMware over the last month or 2, coding up some stuff in C# that interacts with the VI3 web service, and gearing up to take the VI3 VCP exam. And in my preparations, Ubuntu has been indispensable. Now that ESX 3 supports VMFS on iSCSI, I can finally setup something with a decent amount of storage at home using commodity hardware. Specifically, ESX 3 (developer license courtesy of VMTN subscription) running on a P4 3GHz box with IDE drive, 2GB RAM and dual Broadcom PCI GbE NICs, with half a tera of VMFS courtesy of 2 x 250GB SATA2 disks in an Athlon64 X2 box running Ubuntu 6.06.1 Server and the Enterprise iSCSI target. Seriously, it's so easy to install and configure, just read this howto.
This, along with the bare bones Linux build required for VMware Server (search the vmware forums, there are several threads), has effectively had me ditching Microsoft Virtual Server completely... I guess my interest is more in the virtualisation and C# space at the moment, which eliminates my previous needs of having heaps of VM's available (which the differencing disk feature of Virtual Server allowed quite nicely). It will be interesting to see what happens when Microsoft comes out swinging with their Hypervisor and virtual infrastructure management tool, but I can't imagine them knocking VMware off anytime soon... they're just too far ahead of everyone else in the field.
Anyway, I'm decidedly 'over' Linux as a desktop... I'll be running XP into the ground and wait for the next version of Windows, which will be out before XP support ends if Microsoft stick to their "no more 5 years between OSes" mantra. Besides, all the stuff that's interesting to me in Vista / Longhorn (ie .NET 3.0) will be available on XP anyway. I could care less about Aero, DX10 games won't be out for ages, and my shit is locked down so security isn't an issue.
But back to the topic of the post - Ubuntu the Enabler! I've been playing more and more with VMware over the last month or 2, coding up some stuff in C# that interacts with the VI3 web service, and gearing up to take the VI3 VCP exam. And in my preparations, Ubuntu has been indispensable. Now that ESX 3 supports VMFS on iSCSI, I can finally setup something with a decent amount of storage at home using commodity hardware. Specifically, ESX 3 (developer license courtesy of VMTN subscription) running on a P4 3GHz box with IDE drive, 2GB RAM and dual Broadcom PCI GbE NICs, with half a tera of VMFS courtesy of 2 x 250GB SATA2 disks in an Athlon64 X2 box running Ubuntu 6.06.1 Server and the Enterprise iSCSI target. Seriously, it's so easy to install and configure, just read this howto.
This, along with the bare bones Linux build required for VMware Server (search the vmware forums, there are several threads), has effectively had me ditching Microsoft Virtual Server completely... I guess my interest is more in the virtualisation and C# space at the moment, which eliminates my previous needs of having heaps of VM's available (which the differencing disk feature of Virtual Server allowed quite nicely). It will be interesting to see what happens when Microsoft comes out swinging with their Hypervisor and virtual infrastructure management tool, but I can't imagine them knocking VMware off anytime soon... they're just too far ahead of everyone else in the field.
Tuesday, October 31, 2006
In the age of virtualisation, does hardware matter anymore?
Hmmm... some recent developments at my company got me thinking. Basically, the old 'x86 tender' reared it's ugly head again, as it does every few years. In the past, I have been fairly passionate about the hardware that runs the platform I have supported or developed SOE's for. I have actually turned jobs down because they didn't use HP, and resigned from others because they decided to start buying cheaper hardware. I strongly believe you get what you pay for. For example, 2 Engineers worth $50K each do NOT equal one engineer worth $100K. Similarly, if a company decides to go for inferior hardware because it's cheaper, showing a blatant disregard for the work/life balance of their support staff, then they can go fuck themselves. But that kind of thinking belongs in a world without virtualisation.
With virtualisation well entrenched in the roadmap, it didn't seem to phase me so much this time around. All the pain that inferior hardware causes (dodgy hardware, poor hardware design, bad drivers / firmware, frequent driver / firmware updates, frequent engagement of vendor support, etc) pretty much goes away with virtualisation, if your farms are sized intelligently and you are leveraging high availability technologies like HA / DRS on the VMware VI3 platform or clustering with Microsoft Virtual Server.
One of the things I hated the most in my time in the pharma industry was driver validation. Trust me, when a new print driver is released that you really need to fix a nasty bug (I'm talking around the times of NT4 to 2000 migration), and thousands or even tens or hundreds of thousands of people's well being depends upon it's ability to correctly print the micro symbol from an application written for a German MUI that is being run in a manufacturing facility in Kuala Lumpur on a machine with a Malaysian MUI, you WILL care to test it. Then test it again, then have someone else test it, then have another group validate it, then do a UAT, then verify the UAT, then have the validation department verify the UAT, then have the validation department run their own UAT, which is validated by another independent internal QA group... you get the picture. Oh and then do that with the 11 MUI's that your company mandates must be supported. Virtualisation obviously doesn't help with print drivers, but with video, network, array controller, system management processor and chipset drivers taken care of, there's a whole lot less to worry about. I don't want to know what would happen if 10 milligrams of the active ingredient in Viagra went into each pill instead of 10 micrograms. At least they'd all die smiling I guess .
As anyone who has built SOE's for large enterprises knows, hardware differentiation is the cause of most of the work. Having to do hardware enumeration and appropriate driver and software installation causes more work than the actual OS configuration by a long shot. But again, with VM's, this pain goes away. Most of the updates to SOE's surround driver / firmware updates, having to include new hardware models in the build etc. It's all gone now, or going. System recovery? Easy - restore the last snap of the VM. Hell, bring it up on your DR infrastructure instantly because that's where your disk based backup is, right?
No matter how much redundancy you build into a single piece of hardware, you can't account for everything. Ever bought x86 hardware with a redundant motherboard? How about a storage frame with a redundant circuit breaker? Didn't think so. So when you look at it like Google does, hardware just doesn't really matter anymore. We should design / engineer our infrastructure with regular hardware failure as a given. That way, we'll end up with something that is both resilient and cost effective. And we may even get that work/life scale tipped back to horizontal.
With virtualisation well entrenched in the roadmap, it didn't seem to phase me so much this time around. All the pain that inferior hardware causes (dodgy hardware, poor hardware design, bad drivers / firmware, frequent driver / firmware updates, frequent engagement of vendor support, etc) pretty much goes away with virtualisation, if your farms are sized intelligently and you are leveraging high availability technologies like HA / DRS on the VMware VI3 platform or clustering with Microsoft Virtual Server.
One of the things I hated the most in my time in the pharma industry was driver validation. Trust me, when a new print driver is released that you really need to fix a nasty bug (I'm talking around the times of NT4 to 2000 migration), and thousands or even tens or hundreds of thousands of people's well being depends upon it's ability to correctly print the micro symbol from an application written for a German MUI that is being run in a manufacturing facility in Kuala Lumpur on a machine with a Malaysian MUI, you WILL care to test it. Then test it again, then have someone else test it, then have another group validate it, then do a UAT, then verify the UAT, then have the validation department verify the UAT, then have the validation department run their own UAT, which is validated by another independent internal QA group... you get the picture. Oh and then do that with the 11 MUI's that your company mandates must be supported. Virtualisation obviously doesn't help with print drivers, but with video, network, array controller, system management processor and chipset drivers taken care of, there's a whole lot less to worry about. I don't want to know what would happen if 10 milligrams of the active ingredient in Viagra went into each pill instead of 10 micrograms. At least they'd all die smiling I guess .
As anyone who has built SOE's for large enterprises knows, hardware differentiation is the cause of most of the work. Having to do hardware enumeration and appropriate driver and software installation causes more work than the actual OS configuration by a long shot. But again, with VM's, this pain goes away. Most of the updates to SOE's surround driver / firmware updates, having to include new hardware models in the build etc. It's all gone now, or going. System recovery? Easy - restore the last snap of the VM. Hell, bring it up on your DR infrastructure instantly because that's where your disk based backup is, right?
No matter how much redundancy you build into a single piece of hardware, you can't account for everything. Ever bought x86 hardware with a redundant motherboard? How about a storage frame with a redundant circuit breaker? Didn't think so. So when you look at it like Google does, hardware just doesn't really matter anymore. We should design / engineer our infrastructure with regular hardware failure as a given. That way, we'll end up with something that is both resilient and cost effective. And we may even get that work/life scale tipped back to horizontal.
Saturday, October 21, 2006
Jeff Jones, you rock like no other!
One of the security blogs I read often is that of Jeff Jones from Microsoft. He has recently completed the most accurate 'apples vs apples' comparison of Linux (Red Hat and Ubuntu) desktops vs Windows XP.
This is something that has been long overdue. A by-the-numbers analysis of vulnerabilities, using vendor supplied security bulletins and accepted standards body methodology and definitions. [Insert standing ovation]
After pointing one of my work colleagues (a Unix engineer, and a very good one at that) to the initial post, the unsurprising response came back "Yes, but most of those security patches are nothing to do with the operating system - they're 3rd party applications that sit on top.". I retorted that although that may be the case, they are applications included in the distro by the Vendor, supported by the Vendor, patched by the Vendor, and were not applications that are unreasonable to expect on the average installation. Especially not a desktop installation.
However he did get me thinking... we have all lived through the pain of slammer, blaster, sasser and the like, yet having never worked in an environment that had Linux on the desktop or even a significant amount in the datacenter (and the smallest company I have worked for had over 9000 employees - I have spent most of my career working for companies with over 60000 employees), I felt that maybe he did have a point. Where were those anonymous, remotely exploitable vulnerabilities that have hit Windows so hard?
So I asked the question to Jeff, and he responded in his usual level headed, analytical manner, and you can all read the results here.
I've never understood why Linux people feel they can rubbish Windows without knowing a damn thing about it. I have rarely heard a Windows person put shit on Linux, and rightfully so because most of us wouldn't know any better. Conversely, I have heard *plenty* of Unix people deride Linux, and quite frankly they would know. It is from conversations with Unix geeks and my own limited experience with Linux that I derive my unfavourable opinion of it - not from some Microsoft funded 'independent' study or some marketing blurb, and certainly not because it is the status quo amongst the Windows community. But I still won't say a bad thing about it unless provoked.
Now, thanks to Jeff, we have some hard numbers to push back into the faces of anyone who makes that most ill-informed broad generalisation "Windows is less secure than Linux".
But even with such information at hand, as I have said numerous times, any admin worth their salt (*regardless* of platform) knows that it's all about who owns the box, not the OS running on it. It's a shame more people don't think like that... if they did, we probably wouldn't need this kind of analysis in the first place.
This is something that has been long overdue. A by-the-numbers analysis of vulnerabilities, using vendor supplied security bulletins and accepted standards body methodology and definitions. [Insert standing ovation]
After pointing one of my work colleagues (a Unix engineer, and a very good one at that) to the initial post, the unsurprising response came back "Yes, but most of those security patches are nothing to do with the operating system - they're 3rd party applications that sit on top.". I retorted that although that may be the case, they are applications included in the distro by the Vendor, supported by the Vendor, patched by the Vendor, and were not applications that are unreasonable to expect on the average installation. Especially not a desktop installation.
However he did get me thinking... we have all lived through the pain of slammer, blaster, sasser and the like, yet having never worked in an environment that had Linux on the desktop or even a significant amount in the datacenter (and the smallest company I have worked for had over 9000 employees - I have spent most of my career working for companies with over 60000 employees), I felt that maybe he did have a point. Where were those anonymous, remotely exploitable vulnerabilities that have hit Windows so hard?
So I asked the question to Jeff, and he responded in his usual level headed, analytical manner, and you can all read the results here.
I've never understood why Linux people feel they can rubbish Windows without knowing a damn thing about it. I have rarely heard a Windows person put shit on Linux, and rightfully so because most of us wouldn't know any better. Conversely, I have heard *plenty* of Unix people deride Linux, and quite frankly they would know. It is from conversations with Unix geeks and my own limited experience with Linux that I derive my unfavourable opinion of it - not from some Microsoft funded 'independent' study or some marketing blurb, and certainly not because it is the status quo amongst the Windows community. But I still won't say a bad thing about it unless provoked.
Now, thanks to Jeff, we have some hard numbers to push back into the faces of anyone who makes that most ill-informed broad generalisation "Windows is less secure than Linux".
But even with such information at hand, as I have said numerous times, any admin worth their salt (*regardless* of platform) knows that it's all about who owns the box, not the OS running on it. It's a shame more people don't think like that... if they did, we probably wouldn't need this kind of analysis in the first place.
Wednesday, September 20, 2006
Performance Thresholds...
Ahhh, performance thresholds... it's the kind of information you always know the approximate answer to, but rarely remember exactly what the recommendations are. Here's a link that covers the biggies.
Wednesday, September 13, 2006
AMD to Intel MHz conversions...
While putting together some documentation surrounding physical to virtual migrations, I recalled the following handy formula for approximating Intel MHz from AMD MHz. It's basically a reverse engineered derivation of the formula used by AMD for the Athlon64 'Processor Rating' numbers. Now admittedly, that was part marketing BS, to make them more appealing to Joe User who had been brainwashed by the Intel marketing machine into thinking it was all about the MHz (and boy isn't that coming back to haunt them now!). But the 'Processor Rating' number was close enough to the Intel MHz number that the chips held their own in most benchmarks, so it wasn't complete marketing tripe.
This of course only applies to the older PIII / P4 Xeons - not the latest Woodcrest based chips. But then again, the older PIII / P4 Xeons are the most common targets of P2V migrations, so it works nicely.
The formula is:
I know you want to confirm it for yourself, so go ahead - here's a list of a few Athlon64 CPU's with their PR & respective MHz numbers.
So, if you had a dual 1.4GHz PIII Xeon box using 20% CPU on average, and you wanted to know what that would equate to on a single 2.2GHz Opteron, you'd do something like:
Of course there is a boatload of confounding variables, such as how optimised the application is for multi procs, is the Opteron dual core, what if that was a Hyperthreaded P4 Xeon instead of a PIII, and all the architectural differences in the chipsets etc etc. While they are all valid questions, I'm just talking about a very basic rule of thumb here. You've gotta draw a line in the sand somewhere, and there's little point in trying to make a guestimate more accurate - in the end, it's still a guestimate.
If anyone else out there knows of a better / more accurate conversion, please post it in the comments!
This of course only applies to the older PIII / P4 Xeons - not the latest Woodcrest based chips. But then again, the older PIII / P4 Xeons are the most common targets of P2V migrations, so it works nicely.
The formula is:
(AMD MHz + 500) X 1.5 = Intel MHz
I know you want to confirm it for yourself, so go ahead - here's a list of a few Athlon64 CPU's with their PR & respective MHz numbers.
So, if you had a dual 1.4GHz PIII Xeon box using 20% CPU on average, and you wanted to know what that would equate to on a single 2.2GHz Opteron, you'd do something like:
Dual 1.4GHz PIII Average Workload in MHz:
(1400 X 2) X 20% = 560
Estimated Total Intel Equivalent MHz of Single 2.2GHz Opteron:
(2200 + 500) X 1.5 = 4050
Estimated Percentage CPU Utilisation of Single 2.2GHz Opteron:
560 / 4050 = 13.8%
Of course there is a boatload of confounding variables, such as how optimised the application is for multi procs, is the Opteron dual core, what if that was a Hyperthreaded P4 Xeon instead of a PIII, and all the architectural differences in the chipsets etc etc. While they are all valid questions, I'm just talking about a very basic rule of thumb here. You've gotta draw a line in the sand somewhere, and there's little point in trying to make a guestimate more accurate - in the end, it's still a guestimate.
If anyone else out there knows of a better / more accurate conversion, please post it in the comments!
Tuesday, September 12, 2006
Moved to Blogger beta...
With all the beta madness going on, I thought I might as well move the blog to the Blogger beta, which is integrated with Google (in terms of authentication). Doesn't seem to be a whole lot of changes... as long as my shit doesn't get deleted somehow, I guess all will be well!
UPDATE: The new navbar up the top is something I have been hoping for! Finally I can sign in directly from my blog, instead of having to go the Blogger homepage and sign in there. And no more 'republish blog' hassles after a new post... 2 thumbs up!
UPDATE: The new navbar up the top is something I have been hoping for! Finally I can sign in directly from my blog, instead of having to go the Blogger homepage and sign in there. And no more 'republish blog' hassles after a new post... 2 thumbs up!
Saturday, September 09, 2006
Microsoft - I paid for the OS, now get the F@#K out of my face...
It would seem the initial excitement of Vista has worn off... I'm starting to get angry at things that pop up in the OS.
Like the Soundbuzz icon on the Windows Media Player toolbar. I can't get rid of it. I can't imagine how much they must be paying (or is this company owned by Microsoft) to have it imbedded there, but FFS Microsoft - you already earn billions of dollars a year in profits, you charge the end user for your product (and this post relates to the 'Ultimate Edition', the most expensive of the lot), how can you possibly justify planting unremovable advertising in the OS? There's a word for software that does that kind of thing - spyware. There was a recent backlash against 'browzar', where it was labelled 'spyware' because it doesn't give you the option to change the search bar, hence delivering them advertising dollars. Isn't planting an unremovable link to Soundbuzz on the Media Player toolbar the same? Sure I can add more stores, but I can't remove this one.
It also seems that little has been learned from the antitrust lawsuits. Have a look at the Welcome Page. What's that at the bottom? 'Offers from Microsoft'. Now I can only hope that Microsoft isn't stupid enough to disallow 3rd parties advertising in that same space, but at what cost? How about the copies of Windows that aren't purchased via an OEM? There won't be anything non-Microsoft offerings in those cases will there!
What's next then Microsoft? An unremovable adbar in IE? An unremovable ad gadget in the sidebar? Forced advertisements when downloading Windows Updates? Ad technology built into the Windows Installer, so that ads are displayed in the dialog boxes during install? The progress bar replaced with an adbar and a number to indicate percent complete (inconspicously placed of course - wouldn't want to detract from the ads!)?
It's only RC1, and already I'm getting a bad taste in my mouth. Maybe it's time for that Ubuntu install after all.
Like the Soundbuzz icon on the Windows Media Player toolbar. I can't get rid of it. I can't imagine how much they must be paying (or is this company owned by Microsoft) to have it imbedded there, but FFS Microsoft - you already earn billions of dollars a year in profits, you charge the end user for your product (and this post relates to the 'Ultimate Edition', the most expensive of the lot), how can you possibly justify planting unremovable advertising in the OS? There's a word for software that does that kind of thing - spyware. There was a recent backlash against 'browzar', where it was labelled 'spyware' because it doesn't give you the option to change the search bar, hence delivering them advertising dollars. Isn't planting an unremovable link to Soundbuzz on the Media Player toolbar the same? Sure I can add more stores, but I can't remove this one.
It also seems that little has been learned from the antitrust lawsuits. Have a look at the Welcome Page. What's that at the bottom? 'Offers from Microsoft'. Now I can only hope that Microsoft isn't stupid enough to disallow 3rd parties advertising in that same space, but at what cost? How about the copies of Windows that aren't purchased via an OEM? There won't be anything non-Microsoft offerings in those cases will there!
What's next then Microsoft? An unremovable adbar in IE? An unremovable ad gadget in the sidebar? Forced advertisements when downloading Windows Updates? Ad technology built into the Windows Installer, so that ads are displayed in the dialog boxes during install? The progress bar replaced with an adbar and a number to indicate percent complete (inconspicously placed of course - wouldn't want to detract from the ads!)?
It's only RC1, and already I'm getting a bad taste in my mouth. Maybe it's time for that Ubuntu install after all.
Friday, September 08, 2006
n00dles gets one over Windows Server Team blog...
Longhorn build 5600.16834 is out now!!! Not sure if it will be labelled 'RC1', but I'll let y'all know in a few hours.
You read it here first :-D
UPDATE: Well I can't see the words 'RC1' anywhere, but it's certainly a signifcant step forward compared to Beta 2.
You read it here first :-D
UPDATE: Well I can't see the words 'RC1' anywhere, but it's certainly a signifcant step forward compared to Beta 2.
Wednesday, September 06, 2006
Update: Vista RC1 on Virtual Server...
Wow that didn't take long... after attempting in vain to try and disable the wallpaper in the VM for about 15 minutes (the change wallpaper applet crashed everytime), I'm ditching Vista on Virtual Server. Even with 1Gb of RAM, a 16Gb vhd (sitting on a sata2 disk) and the VMAdditions for Vista Beta2, it was completely unusable. It had the CPU pegged at near 100% the whole time - there were no other VM's running and all I was doing was trying to disable the wallpaper!!!
So yeh, Vista RC1 on Virtual Server - just don't do it!
So yeh, Vista RC1 on Virtual Server - just don't do it!
IronPython 1.0 Released...
As if there wasn't enough going on with Vista RC1 and Longhorn build 5600, the IronPython team decided to release 1.0 final! Go grab it here. I've been thinking about having a look at Python for a little while now, so I'll probably have a bit of a look. It may well turn out to be a tough choice for the administrative scripter looking to ditch VBscript - use something like IronPython, or learn C# and leverage the cmdlets functionality of the new shell (which I refuse to call by the name Microsoft gave it).
In the meantime, my Vista RC1 VM (on Virtual Server 2005 R2 x64) just finished installing, time to check it out! Will post up something about that in the next few days...
In the meantime, my Vista RC1 VM (on Virtual Server 2005 R2 x64) just finished installing, time to check it out! Will post up something about that in the next few days...
Monday, September 04, 2006
One word for Vista RC1... sweeeeeeeeeeet!
It's definitely an RC... still quite a few little annoyances and bugs, but it's definitely out of Beta. Beta 2 was so unusable I installed it, used it for a few hours, then promptly blew it away. All while taking Bill's name in vain, and convincing myself that Microsoft was about to lose massive market share on the desktop front. But Vista Build 5600 is going the extra mile on my machine. On first impressions, it rocks!
Sure, there are a few niggling things about parts of the interface. And talk about bloat - it was chewing up ~520Mb or RAM while idling. But to be honest, I don't care. As a gamer, I understand the concept of software built for the next generation of hardware all too well. And that's exactly what Vista is. I don't give a damn that I could get a fully functional Linux box running in 1/10th that amount of memory utilisation - I've got 2GB of RAM in my box, what is the point of not using it!!! In a year or 2's time, when Vista adoption is really hitting it's stride, 2Gb of RAM will be standard on a new machine, maybe even sub-standard. And with terabyte drives for the home just around the corner, I don't care about the 11Gb of disk the OS takes up either.
I've taken a bunch of screenies that you can all check out. Over the coming weeks I'll be getting stuck into some application testing, and no doubt giving the ACT 5.0 beta a workout. Just like I did with earlier versions back when I was a desktop engineer doing packaging and compatibility testing for the early XP rollouts. I'll run it up in Virtual Server for that, it will be a good chance to see what Vista is like without Aero, how it runs as a VM, and whether the beta 2 Vista VM addtions do anything.
And speaking of XP, although Vista is very cool, I don't think there will be widespread adoption for a few years. I also predict XP will become another Windows 98 - favoured by gamers and those who want an OS with less overhead. But then again, Xp still has another 6 years of life before support runs out. I'm sure the successor to Vista will be out by then.
And with regards to my previous post, I've never been so happy to be proven so utterly wrong. I was fully prepped to switch to Linux on my desktop (but stick with Windows servers - it's what I know). But after a few days with Vista RC1, I won't be looking at Linux anytime soon, if ever (not counting the service console of ESX ;-)
Sure, there are a few niggling things about parts of the interface. And talk about bloat - it was chewing up ~520Mb or RAM while idling. But to be honest, I don't care. As a gamer, I understand the concept of software built for the next generation of hardware all too well. And that's exactly what Vista is. I don't give a damn that I could get a fully functional Linux box running in 1/10th that amount of memory utilisation - I've got 2GB of RAM in my box, what is the point of not using it!!! In a year or 2's time, when Vista adoption is really hitting it's stride, 2Gb of RAM will be standard on a new machine, maybe even sub-standard. And with terabyte drives for the home just around the corner, I don't care about the 11Gb of disk the OS takes up either.
I've taken a bunch of screenies that you can all check out. Over the coming weeks I'll be getting stuck into some application testing, and no doubt giving the ACT 5.0 beta a workout. Just like I did with earlier versions back when I was a desktop engineer doing packaging and compatibility testing for the early XP rollouts. I'll run it up in Virtual Server for that, it will be a good chance to see what Vista is like without Aero, how it runs as a VM, and whether the beta 2 Vista VM addtions do anything.
And speaking of XP, although Vista is very cool, I don't think there will be widespread adoption for a few years. I also predict XP will become another Windows 98 - favoured by gamers and those who want an OS with less overhead. But then again, Xp still has another 6 years of life before support runs out. I'm sure the successor to Vista will be out by then.
And with regards to my previous post, I've never been so happy to be proven so utterly wrong. I was fully prepped to switch to Linux on my desktop (but stick with Windows servers - it's what I know). But after a few days with Vista RC1, I won't be looking at Linux anytime soon, if ever (not counting the service console of ESX ;-)
Saturday, September 02, 2006
Last chance, Microsoft (anticipatory thoughts on Vista)...
With the Vista RC1 bits flowing through the tubes to my pc as I write this, I'm wondering how much effort I'll put into getting everything working on it... when I could probably get most stuff working on Linux with the same effort (and feel a little bit better about it).
After a string of pretty woeful beta releases, I am hoping build 5600 is all Vista is cracked up to be, otherwise I'm switching to Ubuntu (and will run any non linux stuff I need in an XP VM).
So I'll build up a Ubuntu 6.06 box and stick on VMware Workstation with an XP VM, and then build up a Vista box (thankyou to whoever invented removable HDD racks!) and see which one gets more usage over the coming months until Vista goes RTM (by which time a newer version of Ubuntu should be out, will will probably have XEN built in!)
Watch this space...
After a string of pretty woeful beta releases, I am hoping build 5600 is all Vista is cracked up to be, otherwise I'm switching to Ubuntu (and will run any non linux stuff I need in an XP VM).
So I'll build up a Ubuntu 6.06 box and stick on VMware Workstation with an XP VM, and then build up a Vista box (thankyou to whoever invented removable HDD racks!) and see which one gets more usage over the coming months until Vista goes RTM (by which time a newer version of Ubuntu should be out, will will probably have XEN built in!)
Watch this space...
Tuesday, August 29, 2006
The end of the monolithic kernel is nigh...
There seems to be a bit of conjecture around the net regarding the whole 'hypervisor' / microkernel architecture thing at the moment. And I have to agree with a lot of it. I can see most OS's splitting off into microkernel architectures, running on hypervisors.
My interest was sparked by this video on Channel9... very cool. And now Microsoft going at lengths to interop with XEN makes so much more sense. Who gives a damn what hypervisor is running underneath... you're still going to need a license for every OS you put on top. And with widespread adoption of virtualisation making the hardware, power and cooling costs drop like never before, I'm sure the number of OS 'instances' is set to go through the roof. I can see it happening already where I work, and I'm sure my company is fairly typical in the large enterprise space.
It's also kind of funny to see the squabbling between Novell and Red Hat with regards to XEN support. Novell will only support SLES on XEN, and Red Hat will only initially support RHEL. Cmon babies, that's no way to promote XEN as an enterprise class hypervisor. Even Microsoft officially supports running certain versions of Linux on Virtual Server 2005 R2 (an application), it's hard to swallow that Linux companies won't support competitor distros running on a hypervisor. Hopefully XEN Source will step in and offer some kind of across the board support for any OS running on XEN, like VMware does with it's products.
And I'll bet when the Microsoft hypervisor drops, they'll be providing support for non-Microsoft OSes too!
My interest was sparked by this video on Channel9... very cool. And now Microsoft going at lengths to interop with XEN makes so much more sense. Who gives a damn what hypervisor is running underneath... you're still going to need a license for every OS you put on top. And with widespread adoption of virtualisation making the hardware, power and cooling costs drop like never before, I'm sure the number of OS 'instances' is set to go through the roof. I can see it happening already where I work, and I'm sure my company is fairly typical in the large enterprise space.
It's also kind of funny to see the squabbling between Novell and Red Hat with regards to XEN support. Novell will only support SLES on XEN, and Red Hat will only initially support RHEL. Cmon babies, that's no way to promote XEN as an enterprise class hypervisor. Even Microsoft officially supports running certain versions of Linux on Virtual Server 2005 R2 (an application), it's hard to swallow that Linux companies won't support competitor distros running on a hypervisor. Hopefully XEN Source will step in and offer some kind of across the board support for any OS running on XEN, like VMware does with it's products.
And I'll bet when the Microsoft hypervisor drops, they'll be providing support for non-Microsoft OSes too!
Thursday, August 10, 2006
Microsoft System Center Virtual Machine Manager...
Following on from that last post, Microsoft have released Beta 1 of their VirtualCenter competitor, System Center Virtual Machine Manager (yes, crappy name). I'm downloading the bits now, and will write up something here in the next week or 2... things are going to get very interesting in the near future, especially when Virtual Server 2005 R2 SP1 ships with full support for Intel VT / AMD Pacifica. Of course I'm sure VMWare server will at least match it in performance, but I'll be interested to see if the gap closes at all on ESX.
Sunday, July 16, 2006
VMWare Server vs Microsoft Virtual Server...
Now that VMWare's free VMWare Server product has gone gold, I thought I'd spend some time evaluating it against Microsoft Virtual Server 2005 R2.
I took 2 identically spec'ed boxes (Athlon64 X2 3800+, 2GB RAM, 160Gb SATA2 disk for Virtual disk files and a separate 40GB IDE disk for the host OS), both running Windows Server 2003 R2 x64 Enterprise Edition. The OS was installed on one box, sysprep'd, then imaged onto the other box so they were identical in all aspects. Virtual Server 2005 R2 x64 Enterprise Edition was installed on one, VMWare Server 1.0.0 was installed on the other.
I then built up a little virtual 'branch office' environment, which ultimately consisted of 4 VM's - a DC, an IIS box with SQL Express 2005 + SP1, a file server, and an ISA 2006 RC1 (Standard Edition) box. All running 2003 R2 Enterprise (32bit), with 384Mb RAM and an 8Gb primary disk (single partition). The virtual disks were contiguous files (thanks to contig.exe from sysinternals), and again all copies of a master sysprep'd disk.
Thoughout the process, I took perfmon metrics of the usual CPU, Memory and Physical disk counters, as well as timing a few installs and boot times. I had planned on doing some more testing after the environment was built, but given how close the 2 products ended up being, I'm not going to bother. The only real differentiator was the background chatter of VMWare Server (when the 4 VM's are running idle, there was about 8% CPU utilisation on the host, versus about 0.5% for Virtual Server), which apparently is linked to Windows x64. Hopefully they can do something about that soon.
Of course, there are many, many differences between the 2 products, and each of those differences differs in importance depending on what you're looking to do. Me personally, after running through a base setup and finding bugger all difference, I'm going to stick with running Virtual Server 2005 R2 at home purely because (a) I'm a Windows engineer and the closest to Unix I get is the Red Hat 7.2 & RHEL 3 service consoles of ESX 2.5x and 3.x respectively (both of which run fine in Virtual Server 2005 R2, in fact Red Hat 7.3, RHEL 3 and RHEL 4 are fully supported) and (b) the differencing disks feature.
For those who don't know what differencing disks are, it's kind of like the snapshots feature of VMWare Server however you can run multiple virtual machines from the 1 'master' virtual disk. So for example, I have one 8Gb master Windows Server 2003 R2 virtual disk which is sysprep'd, and then based on that I have about 23 individual VM's (DC's, a few application clusters, IIS, SQL 2000, SQL 2005, LCS, ISA 2004, Terminal Services, Citrix... you get the idea :-) running off that master, each with their own customisations. But instead of needing 23 x 8Gb disks, I actually only need the 1 x 8Gb master disk, and 23 'differencing' disks, which are bascially the changes I have made from the master. Each differencing disk is about 1Gb in size, depending on what is installed. I do things like create separate little 2Gb or 4Gb fixed secondary disks for things like installing databases or IIS onto, so they are off the C: drive (just as should be done in the enterprise).
Not that I can run all 23 at once, but I could if I had a grunty enough box. Now if I wanted to do this on VMWare Server, I'd need 23 x 8Gb files, and I'd be enabling snapshots for the post sysprep stuff on each one, so I'd probably end up with another 23 x 1Gb files as well. So that would be over 200Gb of disk just for that. And then there would be the space required for the nvram files, etc. With Virtual Server 2005, I can do it with just over 30Gb of space plus the nvram files.
But as I said on the VMWare forums, in an enterprise environment, I wouldn't even consider Microsoft Virtual Server, purely because of the lack of a centralised management tool like Virtual Center. The Virtual Server administration website just doesn't cut it (yes I do have it running on a separate machine). For starters, in an enterprise you'd most likely be running ESX anyway, so having the one management tool for ESX and VMWare Server makes a lot of sense.
In a small / medium business or test lab however, if Windows and Red Hat / Suse Linux was all you needed to run, I'd get straight in there with 2003 x64 and Virtual Server 2005 R2 x64.
I took 2 identically spec'ed boxes (Athlon64 X2 3800+, 2GB RAM, 160Gb SATA2 disk for Virtual disk files and a separate 40GB IDE disk for the host OS), both running Windows Server 2003 R2 x64 Enterprise Edition. The OS was installed on one box, sysprep'd, then imaged onto the other box so they were identical in all aspects. Virtual Server 2005 R2 x64 Enterprise Edition was installed on one, VMWare Server 1.0.0 was installed on the other.
I then built up a little virtual 'branch office' environment, which ultimately consisted of 4 VM's - a DC, an IIS box with SQL Express 2005 + SP1, a file server, and an ISA 2006 RC1 (Standard Edition) box. All running 2003 R2 Enterprise (32bit), with 384Mb RAM and an 8Gb primary disk (single partition). The virtual disks were contiguous files (thanks to contig.exe from sysinternals), and again all copies of a master sysprep'd disk.
Thoughout the process, I took perfmon metrics of the usual CPU, Memory and Physical disk counters, as well as timing a few installs and boot times. I had planned on doing some more testing after the environment was built, but given how close the 2 products ended up being, I'm not going to bother. The only real differentiator was the background chatter of VMWare Server (when the 4 VM's are running idle, there was about 8% CPU utilisation on the host, versus about 0.5% for Virtual Server), which apparently is linked to Windows x64. Hopefully they can do something about that soon.
Of course, there are many, many differences between the 2 products, and each of those differences differs in importance depending on what you're looking to do. Me personally, after running through a base setup and finding bugger all difference, I'm going to stick with running Virtual Server 2005 R2 at home purely because (a) I'm a Windows engineer and the closest to Unix I get is the Red Hat 7.2 & RHEL 3 service consoles of ESX 2.5x and 3.x respectively (both of which run fine in Virtual Server 2005 R2, in fact Red Hat 7.3, RHEL 3 and RHEL 4 are fully supported) and (b) the differencing disks feature.
For those who don't know what differencing disks are, it's kind of like the snapshots feature of VMWare Server however you can run multiple virtual machines from the 1 'master' virtual disk. So for example, I have one 8Gb master Windows Server 2003 R2 virtual disk which is sysprep'd, and then based on that I have about 23 individual VM's (DC's, a few application clusters, IIS, SQL 2000, SQL 2005, LCS, ISA 2004, Terminal Services, Citrix... you get the idea :-) running off that master, each with their own customisations. But instead of needing 23 x 8Gb disks, I actually only need the 1 x 8Gb master disk, and 23 'differencing' disks, which are bascially the changes I have made from the master. Each differencing disk is about 1Gb in size, depending on what is installed. I do things like create separate little 2Gb or 4Gb fixed secondary disks for things like installing databases or IIS onto, so they are off the C: drive (just as should be done in the enterprise).
Not that I can run all 23 at once, but I could if I had a grunty enough box. Now if I wanted to do this on VMWare Server, I'd need 23 x 8Gb files, and I'd be enabling snapshots for the post sysprep stuff on each one, so I'd probably end up with another 23 x 1Gb files as well. So that would be over 200Gb of disk just for that. And then there would be the space required for the nvram files, etc. With Virtual Server 2005, I can do it with just over 30Gb of space plus the nvram files.
But as I said on the VMWare forums, in an enterprise environment, I wouldn't even consider Microsoft Virtual Server, purely because of the lack of a centralised management tool like Virtual Center. The Virtual Server administration website just doesn't cut it (yes I do have it running on a separate machine). For starters, in an enterprise you'd most likely be running ESX anyway, so having the one management tool for ESX and VMWare Server makes a lot of sense.
In a small / medium business or test lab however, if Windows and Red Hat / Suse Linux was all you needed to run, I'd get straight in there with 2003 x64 and Virtual Server 2005 R2 x64.
Friday, July 14, 2006
Tuesday, June 06, 2006
Something Evil for 06.06.06, Day of the Beast...
Here's a great way to kill a Windows Server 2003 + SP1 / R2 box...
1. Create a new reg DWORD TcpTimedWaitDelay in HKLM\System\CurrentControlSet\Services\Tcpip\Parameters
2. Give it a value of 0
3. Reboot
The box will never come back, and give a very ambiguous STOP 0x7F bugcheck. And since it's so early in the boot process it doesn't write a dump file. I found this after reading about the new 'smart TCP port allocation' functionality of the TCPIP stack in 2003+SP1 (and hence R2). I was investigating a problem that I thought may have been caused by the feature, and thought I could effectively switch it off by setting the above. Not sure if it affects 2003 RTM or 2000 in the same way... try it and let me know :-)
1. Create a new reg DWORD TcpTimedWaitDelay in HKLM\System\CurrentControlSet\Services\Tcpip\Parameters
2. Give it a value of 0
3. Reboot
The box will never come back, and give a very ambiguous STOP 0x7F bugcheck. And since it's so early in the boot process it doesn't write a dump file. I found this after reading about the new 'smart TCP port allocation' functionality of the TCPIP stack in 2003+SP1 (and hence R2). I was investigating a problem that I thought may have been caused by the feature, and thought I could effectively switch it off by setting the above. Not sure if it affects 2003 RTM or 2000 in the same way... try it and let me know :-)
Thursday, June 01, 2006
VBScript header...
And while we're on the topic of VBScript, here is what I currently use for a standard script header:
Dim objFSO,objShell,objWMI,objRegEx,strSystemRoot
Set objFSO = CreateObject("Scripting.FileSystemObject")
Set objShell = CreateObject("WScript.Shell")
Set objWMI = GetObject("winmgmts:" & "{impersonationLevel=impersonate}!\\.\root\cimv2")
Set objRegEx = New RegExp
objRegEx.Global = True
objRegEx.IgnoreCase = True
strSystemRoot = objShell.ExpandEnvironmentStrings("%SYSTEMROOT%")
Dim objFSO,objShell,objWMI,objRegEx,strSystemRoot
Set objFSO = CreateObject("Scripting.FileSystemObject")
Set objShell = CreateObject("WScript.Shell")
Set objWMI = GetObject("winmgmts:" & "{impersonationLevel=impersonate}!\\.\root\cimv2")
Set objRegEx = New RegExp
objRegEx.Global = True
objRegEx.IgnoreCase = True
strSystemRoot = objShell.ExpandEnvironmentStrings("%SYSTEMROOT%")
My Favourite Editor has a free version!
I've been using EmEditor for at least 4 years. Initially it was for administrative scripting, but after my favourtie HTML editor (HomeSite) went on the backburner at Macromedia, I started using it for everything. ANd I've never looked back.
Not sure how long the free version has been out, but it's well worth a look. Get it from http://www.emeditor.com/download.htm.
Version 6 should be out soon, with some cool new features. The 'snippets' feature has been a long time coming!
Not sure how long the free version has been out, but it's well worth a look. Get it from http://www.emeditor.com/download.htm.
Version 6 should be out soon, with some cool new features. The 'snippets' feature has been a long time coming!
Monday, May 29, 2006
Virtual Router for Virtual Server 2005 R2...
FreeSCO it seems does not support Virtual Server 2005... version 0.3.5 won't even boot and the developers don't seem to care. Funny thing is that even though Virtual Server uses one of the most compatible NIC chipsets around, the DEC-based Intel 21140, the drivers available for FreeSCO just won't work.
After trying to get it working for an hour or so (I've previously used FreeSCO on VMWare, and it just works straight out of the box), I gave up and started looking for another small linux based router, and found Coyote Linux.
Even though the floppy version is no longer being maintained, it does everything you want and more. They even have a wizard based image creator for Windows - very nice indeed. When you're going through the Wizard, ensure that you select the 'tulip' NIC type for both interfaces. And, just like FreeSCO on VMWare, it works straight out of the box with 16Mb of RAM and no VHD.
Here is a brief how to:
1) Create a new virtual machine with 16MB RAM, no hard disk, no CD/DVD, no SCSI adapter and 2 NICs.
2) Set the floppy drive to always use the image you got from the Coyote wizard
3) Coyote should now start up without a hitch.
4) Add the following line to the firewall configuration file: access Y permit all int-net lan-net all
This will allow all traffic to simply route between the 2 networks.
5) You're done.
Obviously Coyote has been designed to function as much more than a simple router, and some of the other features will no doubt come in handy to simulate DMZ or QoS conditions you get in the real world.
So go and grab it from here, and thanks very much to the good ppl who made it. Give them some business if you can!
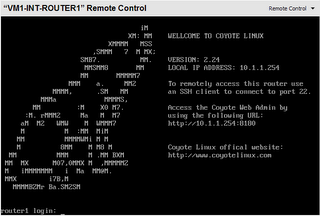
After trying to get it working for an hour or so (I've previously used FreeSCO on VMWare, and it just works straight out of the box), I gave up and started looking for another small linux based router, and found Coyote Linux.
Even though the floppy version is no longer being maintained, it does everything you want and more. They even have a wizard based image creator for Windows - very nice indeed. When you're going through the Wizard, ensure that you select the 'tulip' NIC type for both interfaces. And, just like FreeSCO on VMWare, it works straight out of the box with 16Mb of RAM and no VHD.
Here is a brief how to:
1) Create a new virtual machine with 16MB RAM, no hard disk, no CD/DVD, no SCSI adapter and 2 NICs.
2) Set the floppy drive to always use the image you got from the Coyote wizard
3) Coyote should now start up without a hitch.
4) Add the following line to the firewall configuration file: access Y permit all int-net lan-net all
This will allow all traffic to simply route between the 2 networks.
5) You're done.
Obviously Coyote has been designed to function as much more than a simple router, and some of the other features will no doubt come in handy to simulate DMZ or QoS conditions you get in the real world.
So go and grab it from here, and thanks very much to the good ppl who made it. Give them some business if you can!

Monday, May 15, 2006
Adding Console fonts...
I recently switched to using the newish Consolas font from Microsoft for VS2005 / text editors. It's a nice font, and I was wondering how I could get it into the console if it was even possible. Turns out it is, with this 'unsupported' hack from Microsoft
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Console\TrueTypeFont]
"00"="Consolas"
KB article is here.
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Console\TrueTypeFont]
"00"="Consolas"
KB article is here.
Saturday, May 13, 2006
Goodbye Array... hello Disconnected DataSet!
I've always hated working with Arrays in VBScript... they're fiddly at the best of times. And if you ever have to sort the data in an array (let alone a multidimensional one), you're pretty much screwed. Enter the Disconnected DataSet.
Instead of building an array and stuffing data into it, you can create an in memory database using ADO that only exists while the script executes. I'm sure from an application perspective there are tons of risks associated with using such a technique to actually talk back to real database at some point, but for administrative scripting, it's a godsend.
So say you wanted to query all the services on a machine using WMI, and list them in order of the state they were in as opposed to the alphabetical order of the service name (which is the order WMI would return the query in). You would simply:
Const adVarChar = 200
Const MaxCharacters = 255
Set DataList = CreateObject("ADOR.Recordset")
DataList.Fields.Append "ServiceName", adVarChar, MaxCharacters
DataList.Fields.Append "ServiceState", adVarChar, MaxCharacters
DataList.Open
strComputer = "."
Set objWMIService = GetObject("winmgmts:" _
& "{impersonationLevel=impersonate}!\\" & strComputer& "\root\cimv2")
Set colServices = objWMIService.ExecQuery _
("SELECT * FROM Win32_Service")
For Each Service in colServices
DataList.AddNew
DataList("ServiceName") = Service.Name
DataList("ServiceState") = Service.State
DataList.Update
Next
DataList.Sort = "ServiceState"
DataList.MoveFirst
Do Until DataList.EOF
Wscript.Echo DataList.Fields.Item("ServiceName") _
& vbTab & DataList.Fields.Item("ServiceState")
DataList.MoveNext
Loop
Here is the link to where that code came from... I am sure I will be using this technique a lot from now on.
Instead of building an array and stuffing data into it, you can create an in memory database using ADO that only exists while the script executes. I'm sure from an application perspective there are tons of risks associated with using such a technique to actually talk back to real database at some point, but for administrative scripting, it's a godsend.
So say you wanted to query all the services on a machine using WMI, and list them in order of the state they were in as opposed to the alphabetical order of the service name (which is the order WMI would return the query in). You would simply:
Const adVarChar = 200
Const MaxCharacters = 255
Set DataList = CreateObject("ADOR.Recordset")
DataList.Fields.Append "ServiceName", adVarChar, MaxCharacters
DataList.Fields.Append "ServiceState", adVarChar, MaxCharacters
DataList.Open
strComputer = "."
Set objWMIService = GetObject("winmgmts:" _
& "{impersonationLevel=impersonate}!\\" & strComputer& "\root\cimv2")
Set colServices = objWMIService.ExecQuery _
("SELECT * FROM Win32_Service")
For Each Service in colServices
DataList.AddNew
DataList("ServiceName") = Service.Name
DataList("ServiceState") = Service.State
DataList.Update
Next
DataList.Sort = "ServiceState"
DataList.MoveFirst
Do Until DataList.EOF
Wscript.Echo DataList.Fields.Item("ServiceName") _
& vbTab & DataList.Fields.Item("ServiceState")
DataList.MoveNext
Loop
Here is the link to where that code came from... I am sure I will be using this technique a lot from now on.
Sunday, April 30, 2006
Dual boot Windows PE 2005 / Windows Server 2003 R2
It's a LOT easier than you think... forget about anything involving copying setupldr or anything else from the PE source, or using Barts peldr util. All you have to do is:
1. Install the Recovery Console
2. Copy BOOTSECT.DAT from the cmdcons directory to the root of C:
3. Copy your PE I386 directory to the root of C:
4. Rename the PE I386 directory to MININT
5. Copy the winbom.ini from MININT to the root C:
6. Add a line C:\BOOTSECT.DAT = "Windows PE" /MININT to boot.ini
And that's it. Obviously when you boot into this PE environment, the C: drive will actually be X:. I'm not sure if there's another way to get it booting straight into RAM off an ISO without replacing the native 2003 ntldr, but that sure would be nice.
Note: I'm not sure if you actually need to install the Recovery Console, but you at least need the bootsect.dat and cmldr files in the root of C. If you get an 'ntldr missing' error, it's actually the cmldr that you are missing.
1. Install the Recovery Console
2. Copy BOOTSECT.DAT from the cmdcons directory to the root of C:
3. Copy your PE I386 directory to the root of C:
4. Rename the PE I386 directory to MININT
5. Copy the winbom.ini from MININT to the root C:
6. Add a line C:\BOOTSECT.DAT = "Windows PE" /MININT to boot.ini
And that's it. Obviously when you boot into this PE environment, the C: drive will actually be X:. I'm not sure if there's another way to get it booting straight into RAM off an ISO without replacing the native 2003 ntldr, but that sure would be nice.
Note: I'm not sure if you actually need to install the Recovery Console, but you at least need the bootsect.dat and cmldr files in the root of C. If you get an 'ntldr missing' error, it's actually the cmldr that you are missing.
Tuesday, April 25, 2006
Moving the Admin Tools shortcuts...
It's really annoying that even after doing this...
@echo off
echo Moving Admin Tools Shortcuts...
move /Y "%ALLUSERSPROFILE%\Start Menu\Programs\Administrative Tools" "%ALLUSERSPROFILE%\Start Menu\Administrative Tools"
echo Setting Admin Tools Shortcut location in registry...
REG ADD "HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders" /v "Common Administrative Tools" /t REG_SZ /d "%ALLUSERSPROFILE%\Start Menu\Administrative Tools" /F
REG ADD "HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders" /v "Common Administrative Tools" /t REG_EXPAND_SZ /d "%%ALLUSERSPROFILE%%\Start Menu\Administrative Tools" /F
... if you install something else that drops a shortcut into the Administrative Tools directory, like IIS for example, it still puts the shortcuts into %ALLUSERSPROFILE%\Start Menu\Programs\Administrative Tools.
Really annoying.
@echo off
echo Moving Admin Tools Shortcuts...
move /Y "%ALLUSERSPROFILE%\Start Menu\Programs\Administrative Tools" "%ALLUSERSPROFILE%\Start Menu\Administrative Tools"
echo Setting Admin Tools Shortcut location in registry...
REG ADD "HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Shell Folders" /v "Common Administrative Tools" /t REG_SZ /d "%ALLUSERSPROFILE%\Start Menu\Administrative Tools" /F
REG ADD "HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\User Shell Folders" /v "Common Administrative Tools" /t REG_EXPAND_SZ /d "%%ALLUSERSPROFILE%%\Start Menu\Administrative Tools" /F
... if you install something else that drops a shortcut into the Administrative Tools directory, like IIS for example, it still puts the shortcuts into %ALLUSERSPROFILE%\Start Menu\Programs\Administrative Tools.
Really annoying.
Monday, April 17, 2006
Copy Local Policies to other machines...
Here's how I have done it / seen it done
1. Configure the local policy on one machine
2. Copy the %systemroot%\System32\GroupPolicy folder to somewhere on the network / your distribution share / whatever
3. On each target machine, assuming the 'master' GroupPolicy directory is located at D:\GroupPolicy, do
attrib -H %systemroot%\system32\GroupPolicy
xcopy D:\GroupPolicy\* %SystemRoot%\system32\GroupPolicy /e /v /c /i /h /r /y
attrib +H %systemroot%\system32\GroupPolicy
Reboot the target machine and all should be well.
1. Configure the local policy on one machine
2. Copy the %systemroot%\System32\GroupPolicy folder to somewhere on the network / your distribution share / whatever
3. On each target machine, assuming the 'master' GroupPolicy directory is located at D:\GroupPolicy, do
attrib -H %systemroot%\system32\GroupPolicy
xcopy D:\GroupPolicy\* %SystemRoot%\system32\GroupPolicy /e /v /c /i /h /r /y
attrib +H %systemroot%\system32\GroupPolicy
Reboot the target machine and all should be well.
Saturday, March 25, 2006
Scripting Certificate Requests with a Subject Alternative Name...
Man I can't believe how difficult it was to track this down... it seems everywhere on the web has 99% of the info, but give examples for uses like DC auth and SmartCard enrollment... I finally figured it out with a bit of trial and error though, so here's how you would issue a certificate for plain old server authentication (ie SSL) with a subject alternative name.
First, create a certreq.inf file with the following contents:
Next, create your request file by running certreq on the target machine as follows:
certreq -new c:\certreq.inf c:\servercert.req
This requires certreq from the 2003 admin tools (i think... maybe it's the reskit or support tools... can't remember) and the certreq.inf file in the root of C.
Jump onto your issuing CA (it is Windows Server 2003, isn't it?) and run the following (the first command should all be on one line):
certutil -setreg policy\EditFlags +EDITF_ATTRIBUTESUBJECTALTNAME2
net stop "certificate services"
net start "certificate services"
Now take that servercert.req file and transfer it to your issuing CA. On the issuing CA, run (again, all on one line):
certreq -q -attrib "SAN:DNS=whatever.alternate.name.you.want" -submit c:\servercert.req
And that's it. Man I lost some sleep over that... glad it's sorted!
First, create a certreq.inf file with the following contents:
[NewRequest]
Subject = "CN=hostname"
KeySpec = 1
KeyLength = 1024
Exportable = FALSE
MachineKeySet = TRUE
SMIME = FALSE
PrivateKeyArchive = FALSE
UserProtected = FALSE
UseExistingKeySet = FALSE
ProviderName = "Microsoft RSA SChannel Cryptographic Provider"
ProviderType = 12
RequestType = PKCS10
KeyUsage = 0xa0
[EnhancedKeyUsageExtension]
OID = 1.3.6.1.5.5.7.3.1
Next, create your request file by running certreq on the target machine as follows:
certreq -new c:\certreq.inf c:\servercert.req
This requires certreq from the 2003 admin tools (i think... maybe it's the reskit or support tools... can't remember) and the certreq.inf file in the root of C.
Jump onto your issuing CA (it is Windows Server 2003, isn't it?) and run the following (the first command should all be on one line):
certutil -setreg policy\EditFlags +EDITF_ATTRIBUTESUBJECTALTNAME2
net stop "certificate services"
net start "certificate services"
Now take that servercert.req file and transfer it to your issuing CA. On the issuing CA, run (again, all on one line):
certreq -q -attrib "SAN:DNS=whatever.alternate.name.you.want" -submit c:\servercert.req
And that's it. Man I lost some sleep over that... glad it's sorted!
Wednesday, March 22, 2006
SQL Server 2005 Express setup...
So anyway I decided it's about time I start installing SQL Server 2005 Express wherever I can, instead of MSDE. There are a lot of changes in the installer from MSDE. Aside from the thousands of parameters, there are some other fundamental changes like INSTANCENAME being a required parameter and 3 user accounts are required to install the core SQL_Engine component.
So here is how to automate that:
1. First create an ini file, lets call it 'sqlsetup.ini'
2. Copy the following into sqlsetup.ini
3. That's it - you should now be able to run a silent unattended setup with:
start /wait setup.exe /qb /settings D:\sqlsetup.ini
So here is how to automate that:
1. First create an ini file, lets call it 'sqlsetup.ini'
2. Copy the following into sqlsetup.ini
[Options]
INSTALLSQLDIR=E:\SQLEXPRESSADDLOCAL=SQL_Engine,SQL_Data_Files,SQL_Replication,Client_Components,Connectivity
INSTANCENAME=MSSQLSERVER
SQLBROWSERACCOUNT="NT AUTHORITY\NETWORK SERVICE"
SQLACCOUNT="NT AUTHORITY\SYSTEM"
AGTACCOUNT="NT AUTHORITY\LOCAL SERVICE"
SQLAUTOSTART=1
SAPWD=P@ssw0rd
DISABLENETWORKPROTOCOLS=2
3. That's it - you should now be able to run a silent unattended setup with:
start /wait setup.exe /qb /settings D:\sqlsetup.ini
Monday, March 20, 2006
Altiris Deployment Server Setup Error
Funnily enough, the Altiris Deployment Server 6.5 setup is able to determine that SQL is installed on a machine, and determine the instance name, but can't determine if the correct network connectivity is present for it to actually work.
So when going through the install you think all is well, until you get a "Setup was unable to run "DBinstaller.exe" to create the "express" database" and get told the installer will quit.
Rather cryptic... and it's because no network protocols are enabled by default in MSDE 2000 + SP4 installs (ie DISABLENETWORKPROTOCOLS=1 by default now). The way to fix the error is to go into %programfiles%\Microsoft SQL Server\80\Tools\Binn and run srvnetcn.exe. You'll see all network protocols disabled by default - just enable TCP/IP, restart the SQL Server service and then re-run the DS 6.5 install, and all actually will be well.
So when going through the install you think all is well, until you get a "Setup was unable to run "DBinstaller.exe" to create the "express" database" and get told the installer will quit.
Rather cryptic... and it's because no network protocols are enabled by default in MSDE 2000 + SP4 installs (ie DISABLENETWORKPROTOCOLS=1 by default now). The way to fix the error is to go into %programfiles%\Microsoft SQL Server\80\Tools\Binn and run srvnetcn.exe. You'll see all network protocols disabled by default - just enable TCP/IP, restart the SQL Server service and then re-run the DS 6.5 install, and all actually will be well.
Sunday, March 19, 2006
Unlimited Linux iSCSI Target in 5 minutes
After finding there were no suitable Windows iSCSI products around for me to play with at home, I ended up using a Linux one and had it running in VMWare quicker than you can say 'iscsitarget.sourceforge.net'. Here's how:
1. Download the free RHEL4 Virtual Machine from here.
2. Add another virtual SCSI disk to the prebuilt VM.
3. Follow these installation instructions to download and install iSCSI Enterprise Target.
4. Use the following as your ietd.conf file
5. Restart the iscsi service with service iscsi-target restart
6. Configure your iSCSI initiator now - if you need a hand have a look at this
And that's it. I wasted more time looking for a trial version of a Windows based product that had a reasonable asking price for the full version, and actually felt like I learned a little something in the process.
Now all I have to do is download Fedora Core 4 and do the same on a physical box.
1. Download the free RHEL4 Virtual Machine from here.
2. Add another virtual SCSI disk to the prebuilt VM.
3. Follow these installation instructions to download and install iSCSI Enterprise Target.
4. Use the following as your ietd.conf file
Target iqn.2006-03.local.domain:rhel4.storage.lun1
# Users, who can access this target
# (no users means anyone can access the target)
#IncomingUser
#OutgoingUser
#Lun definition
Lun 0 Path=/dev/sdb
# Alias name for this target
Alias GOiSCSI
5. Restart the iscsi service with service iscsi-target restart
6. Configure your iSCSI initiator now - if you need a hand have a look at this
And that's it. I wasted more time looking for a trial version of a Windows based product that had a reasonable asking price for the full version, and actually felt like I learned a little something in the process.
Now all I have to do is download Fedora Core 4 and do the same on a physical box.
Tuesday, March 14, 2006
Using Poolmon to find kernel memory leaks...
Just so it's easier for me to find, here is the technet site that covers all the Support Tools
http://technet2.microsoft.com/WindowsServer/en/Library/eb0d5bd1-89c3-4ee7-975f-596b2e37e3aa1033.mspx
I was going to post up some stuff about using Poolmon and Memsnap, but you might as well just read the overview, syntax and example pages for these tools from the Technet site! Just make sure you enable gflags first on a Windows 2000 box, which requires a reboot before it becomes active. It's on by default in 2003.
I will add some small things... so when you've identified and offending tag, if the tag name isn't in pooltag.txt then open %windir%\System32\Drivers and do a search within files for the tag name. So thats search for files named '*' containing text 'tag'... or you could use findstr /m /l tag *.sys too I guess.
Also, while poolmon.exe comes with the Support Tools, pooltag.txt actually comes with both the Resource Kit and WinDbg. It's not a static file, so your best bet is to go with the most recent version, which is usually WinDbg. You'll find it in the /triage subdirectory.
Speaking of WinDbg, here is the symbol search path I always use (and lose - that's why it's going up here!)
C:\Windows\symbols\2000BASE;C:\Windows\symbols\2000SP4;
C:\Windows\symbols\2000SP4U1;C:\Windows\symbols\2003BASE;
C:\Windows\symbols\2003SP1;
SRV*C:\Windows\symbols\download*http://msdl.microsoft.com/download/symbols
Hmmm I'm gonna have to do something about this stylesheet eh!
http://technet2.microsoft.com/WindowsServer/en/Library/eb0d5bd1-89c3-4ee7-975f-596b2e37e3aa1033.mspx
I was going to post up some stuff about using Poolmon and Memsnap, but you might as well just read the overview, syntax and example pages for these tools from the Technet site! Just make sure you enable gflags first on a Windows 2000 box, which requires a reboot before it becomes active. It's on by default in 2003.
I will add some small things... so when you've identified and offending tag, if the tag name isn't in pooltag.txt then open %windir%\System32\Drivers and do a search within files for the tag name. So thats search for files named '*' containing text 'tag'... or you could use findstr /m /l tag *.sys too I guess.
Also, while poolmon.exe comes with the Support Tools, pooltag.txt actually comes with both the Resource Kit and WinDbg. It's not a static file, so your best bet is to go with the most recent version, which is usually WinDbg. You'll find it in the /triage subdirectory.
Speaking of WinDbg, here is the symbol search path I always use (and lose - that's why it's going up here!)
C:\Windows\symbols\2000BASE;C:\Windows\symbols\2000SP4;
C:\Windows\symbols\2000SP4U1;C:\Windows\symbols\2003BASE;
C:\Windows\symbols\2003SP1;
SRV*C:\Windows\symbols\download*http://msdl.microsoft.com/download/symbols
Hmmm I'm gonna have to do something about this stylesheet eh!
Sunday, March 05, 2006
Remove Removed Devices...
One of the most annoying errors IMHO is the one that you get when you change out a NIC (or remove a NIC from a VM) and try to reuse the IP address on the same machine.
So to get rid of that, first set the following machine environment variable:
DEVMGR_SHOW_NONPRESENT_DEVICES
... and give it a value of 1
I'll seriously consider adding this to the next SOE I work on, probably with a
setx DEVMGR_SHOW_NONPRESENT_DEVICES 1 -m
This will allow you to see the removed devices in Device Manager when you go into the View menu and tick 'Show Hidden Devices'
So to get rid of that, first set the following machine environment variable:
DEVMGR_SHOW_NONPRESENT_DEVICES
... and give it a value of 1
I'll seriously consider adding this to the next SOE I work on, probably with a
setx DEVMGR_SHOW_NONPRESENT_DEVICES 1 -m
This will allow you to see the removed devices in Device Manager when you go into the View menu and tick 'Show Hidden Devices'
Monday, February 27, 2006
Miscellanea...
A bunch of stuff I need from time to time, but am never sure where to find it...
First, some XP reg tweaks I like to use...
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Security Center]
"FirstRunDisabled"=dword:00000001
"AntiVirusDisableNotify"=dword:00000001
"FirewallDisableNotify"=dword:00000001
"UpdatesDisableNotify"=dword:00000001
[HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer]
"NoSimpleStartMenu"=dword:00000001
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\Advanced]
"CascadeControlPanel"="YES"
"StartMenuAdminTools"=dword:00000001
Now how to silent install MSDE 2000... drop a setup.ini with the following entries into the same directory as setup.exe:
[Options]
SAPWD="AStrongPassword"
DATADIR="D:\MSDE\Data\"
TARGETDIR="D:\MSDE\Bin\"
;INSTANCENAME=AnInstanceName
;SECURITYMODE=SQL
;DISABLENETWORKPROTOCOLS=0
Run setup and reboot when it's finished.
And if you wanted to setup SQL 2000 server unattended style, you would first create the sqlsetup.iss using the SQL Server setup program (Advanced install option - it drops the resulting file into %windir%) and then fire off a:
start /wait setupsql.exe -s -f1 %windir%\sqlsetup.iss -sms
Installing anything is always best done via script, like IIS. First create a file with the following contents:
[Components]
iis_common=On
iis_inetmgr=On
iis_www=On
iis_ftp=Off
iis_htmla=Off
iis_doc=Off
iis_pwmgr=Off
iis_smtp=Off
iis_smtp_docs=Off
iis_nntp=Off
iis_nntp_docs=Off
iisdbg=Off
;For IIS 5 Frontpage Extensions, uncomment below
;Fp=Off
;For IIS 6 Frontpage Extensions, uncomment below
;fp_extensions=Off
[InternetServer]
PathWWWRoot=D:\Inetpub\wwwroot
;PathFTPRoot=D:\Inetpub\ftproot
Save it to, say, the root of C, and if it was named iisunattend.txt, shell out and run:
sysocmgr /i:%windir%\inf\sysoc.inf /u:c:\iisunattend.txt
Renaming the 'My Computer' and 'My Network Places' to something more meaningful is always useful. In a shell script,
:: Set 'My Computer' to be %username% on %computername%
echo.
echo Modifying My Computer name...
reg.exe ADD HKCR\CLSID\{20D04FE0-3AEA-1069-A2D8-08002B30309D} /v LocalizedString /t REG_EXPAND_SZ /d "%%UserName%% on %%ComputerName%%" /F
:: Set 'My Network Places' to be %userdomain%
echo.
echo Modifying My Network Places name...
reg.exe ADD HKCR\CLSID\{208D2C60-3AEA-1069-A2D7-08002B30309D} /v LocalizedString /t REG_EXPAND_SZ /d "%%UserDomain%%" /F
Also useful is setting files without an extension to open with Notepad. In a shell script:
:: Set files with no extensions to open with Notepad
echo.
echo Setting file association for files with no extension...
REG ADD HKCR\.\shell\open\command\ /ve /t REG_SZ /d "notepad.exe %%1" /F
ANd to illustrate why shell scripting in Windows 2000/XP/2003 bites the fat one, here is what you would have to do if you wanted to execute something and then parse the single line of returned output:
for /f "usebackq tokens=*" %%i in (`plink -ssh -l -pw nixhost.corp cat /tmp/afile.tmp`) do (if "%%i"=="something" GOTO :DOSOMETHING)
Glad I can use VBScript for anything more complicated than a for statement.
Finally, here's an example of how you can use subinacl to grant the local Users group the necessary registry and service permissions to run perfmon remotely:
echo Granting Users Read access to Perlib registry key...
echo.
subinacl /subkeyreg "HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Perflib" /grant=Users=R
subinacl /subkeyreg "HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\SecurePipeServers\winreg" /grant=Users=R
echo Granting Users Full Control of sysmonlog service...
echo.
subinacl /service sysmonlog /grant=Users=F
echo All operations completed!
echo.
That's about it for now... I'll no doubt make more of these kinds of posts so I can easily access them if necessary.
First, some XP reg tweaks I like to use...
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Security Center]
"FirstRunDisabled"=dword:00000001
"AntiVirusDisableNotify"=dword:00000001
"FirewallDisableNotify"=dword:00000001
"UpdatesDisableNotify"=dword:00000001
[HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer]
"NoSimpleStartMenu"=dword:00000001
[HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\Advanced]
"CascadeControlPanel"="YES"
"StartMenuAdminTools"=dword:00000001
Now how to silent install MSDE 2000... drop a setup.ini with the following entries into the same directory as setup.exe:
[Options]
SAPWD="AStrongPassword"
DATADIR="D:\MSDE\Data\"
TARGETDIR="D:\MSDE\Bin\"
;INSTANCENAME=AnInstanceName
;SECURITYMODE=SQL
;DISABLENETWORKPROTOCOLS=0
Run setup and reboot when it's finished.
And if you wanted to setup SQL 2000 server unattended style, you would first create the sqlsetup.iss using the SQL Server setup program (Advanced install option - it drops the resulting file into %windir%) and then fire off a:
start /wait setupsql.exe -s -f1 %windir%\sqlsetup.iss -sms
Installing anything is always best done via script, like IIS. First create a file with the following contents:
[Components]
iis_common=On
iis_inetmgr=On
iis_www=On
iis_ftp=Off
iis_htmla=Off
iis_doc=Off
iis_pwmgr=Off
iis_smtp=Off
iis_smtp_docs=Off
iis_nntp=Off
iis_nntp_docs=Off
iisdbg=Off
;For IIS 5 Frontpage Extensions, uncomment below
;Fp=Off
;For IIS 6 Frontpage Extensions, uncomment below
;fp_extensions=Off
[InternetServer]
PathWWWRoot=D:\Inetpub\wwwroot
;PathFTPRoot=D:\Inetpub\ftproot
Save it to, say, the root of C, and if it was named iisunattend.txt, shell out and run:
sysocmgr /i:%windir%\inf\sysoc.inf /u:c:\iisunattend.txt
Renaming the 'My Computer' and 'My Network Places' to something more meaningful is always useful. In a shell script,
:: Set 'My Computer' to be %username% on %computername%
echo.
echo Modifying My Computer name...
reg.exe ADD HKCR\CLSID\{20D04FE0-3AEA-1069-A2D8-08002B30309D} /v LocalizedString /t REG_EXPAND_SZ /d "%%UserName%% on %%ComputerName%%" /F
:: Set 'My Network Places' to be %userdomain%
echo.
echo Modifying My Network Places name...
reg.exe ADD HKCR\CLSID\{208D2C60-3AEA-1069-A2D7-08002B30309D} /v LocalizedString /t REG_EXPAND_SZ /d "%%UserDomain%%" /F
Also useful is setting files without an extension to open with Notepad. In a shell script:
:: Set files with no extensions to open with Notepad
echo.
echo Setting file association for files with no extension...
REG ADD HKCR\.\shell\open\command\ /ve /t REG_SZ /d "notepad.exe %%1" /F
ANd to illustrate why shell scripting in Windows 2000/XP/2003 bites the fat one, here is what you would have to do if you wanted to execute something and then parse the single line of returned output:
for /f "usebackq tokens=*" %%i in (`plink -ssh -l
Glad I can use VBScript for anything more complicated than a for statement.
Finally, here's an example of how you can use subinacl to grant the local Users group the necessary registry and service permissions to run perfmon remotely:
echo Granting Users Read access to Perlib registry key...
echo.
subinacl /subkeyreg "HKEY_LOCAL_MACHINE\Software\Microsoft\Windows NT\CurrentVersion\Perflib" /grant=Users=R
subinacl /subkeyreg "HKEY_LOCAL_MACHINE\System\CurrentControlSet\Control\SecurePipeServers\winreg" /grant=Users=R
echo Granting Users Full Control of sysmonlog service...
echo.
subinacl /service sysmonlog /grant=Users=F
echo All operations completed!
echo.
That's about it for now... I'll no doubt make more of these kinds of posts so I can easily access them if necessary.
Subscribe to:
Comments (Atom)